- Published: Nov 21,2025
Jamf Executive Threat Protection: AI Analysis Beta Ushers in a New Era of Mobile Forensics

Jamf has taken another major step forward in mobile cybersecurity with the introduction of AI Analysis, now available in beta for all Jamf Executive Threat Protection cloud customers. This new capability brings automated, expert-level forensic insights directly into the hands of security teams, drastically reducing investigation time and improving threat response.
What is Jamf Executive Threat Protection?
Jamf Executive Threat Protection is a specialized mobile forensics solution built to detect the most sophisticated attacks aimed at iOS and Android devices. It’s specifically designed for individuals who face elevated risk, such as corporate executives, government officials, journalists, and frequent travelers, who may be targeted by advanced spyware or zero-day exploits.
With mercenary spyware continuing to rise globally (Apple has issued threat notifications to users in over 150 countries since 2021), organizations need deeper visibility into mobile device behavior without compromising user privacy. Jamf’s solution empowers SOC and forensics teams with advanced threat detection while ensuring no Personally Identifiable Information (PII) is exposed.
Introducing AI Analysis (Beta)
Debuted on the JNUC 2025 stage, AI Analysis adds a virtual forensic expert to the workflow, one that can analyze device anomalies, crashes, and potential threat indicators in minutes.
Instead of manually sifting through raw telemetry, logs, and crash data, teams can now trigger a full analysis with a single click.
How AI Analysis Works
Figure 1.1 AI Analysis conducts research on a device's status.
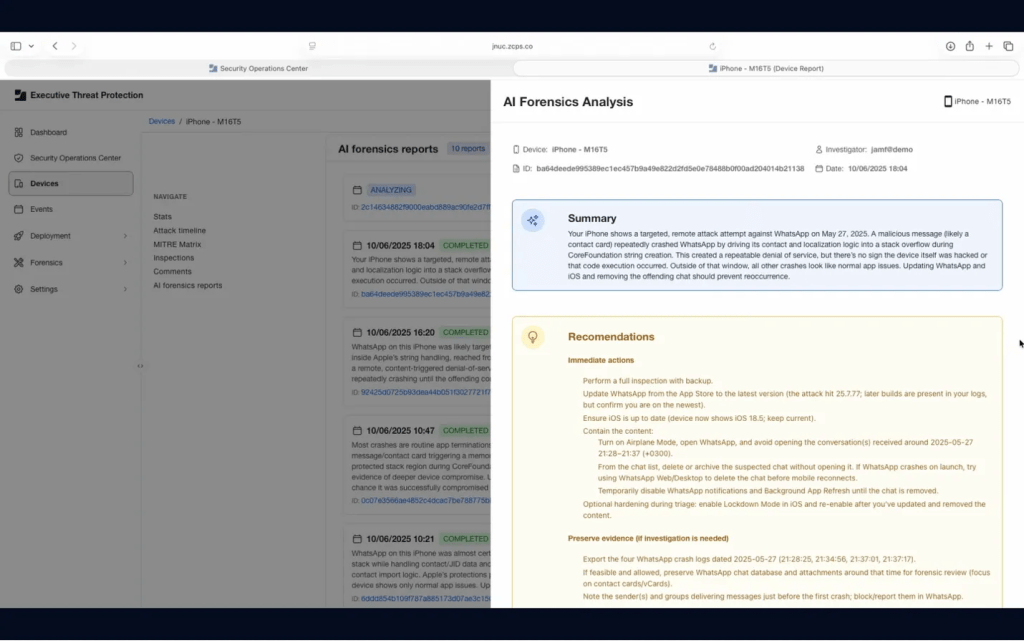
Figure 1.2 AI Analysis details its summary and recommendations for the next steps for the device to stay secure.
Activate the AI Analysis Scan
Analysts simply click the AI Analysis button on the device record within the Jamf console.Automated Forensic Research
The AI engine evaluates the device’s behavior, correlates data patterns, and identifies suspicious activity that may otherwise take hours to detect manually.Clear Incident Summary
Upon completion, the system generates:A plain-language summary of findings
Context behind anomalies or threats
Recommendations for next steps to keep the device secure
Downloadable Detailed Report
Teams can export a complete forensic report for escalation, internal review, or documentation.
Why This Matters for Security Teams
AI Analysis dramatically reduces the time and expertise required to understand whether unusual behavior indicates a real threat or harmless device activity. Benefits include:
Faster escalation and response times
Reduced reliance on specialized forensic expertise
Clear guidance for next steps after an incident
Consistent analysis across all devices
In short, the feature bridges the gap between raw mobile telemetry and actionable cybersecurity intelligence.
Related Post
Want Access to the AI Analysis Beta?
Organizations interested in enabling the AI Analysis beta can contact their Jamf representative for onboarding.
